Overview
The blog post explores the use of AWS Secrets Manager - what problem it solves, how we store secrets using the AWS Management Console, configurations required for reading secrets and application code to read secrets.
The problem of managing secrets
Application usually need to use user-ids and passwords to access various resources like databases. Suppose your solution comprises of multiple application each application has a copy of these credentials.
The situation is made worse when the solution is distributed across multiple machines. This increases the surface attack area from where a credential may be leaked.
What about distribution? What happens when the password for a particular database user is changed? How do we update secrets in all the affected applications?
AWS Secrets Manager
AWS Secrets Manager centralizes storage of secrets so application need not take on the added responsibility of storing secrets securely. AWS Secrets Managers also helps you to with best practices such a rotating keys periodically.
Steps to use AWS Secrets Manager
Identify the secret
The first activity is to identify those bits of information which need to be protected from leaking like user-ids, passwords, encryption keys and others. This type of information should be removed from code, application configuration files and other places and should be stored in AWS Secrets Manager instead.
Store the secret in Secrets Manager
We'll store a key value pair 'foo' & 'bar'. Open the AWS Management Console and navigate to the AWS Secrets Manager service. The name used in this example is 'for/testing'.
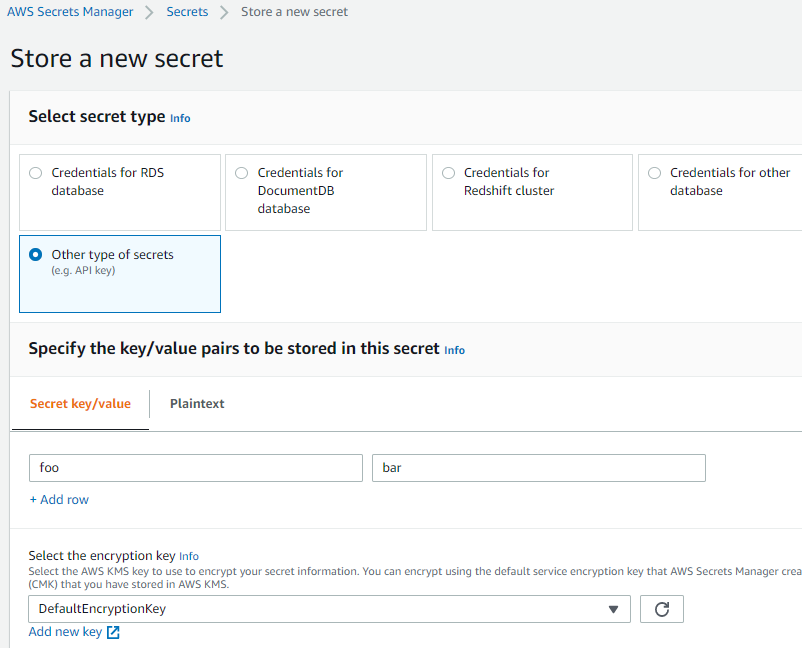
Copy the ARN of the secret in a text editor as we'll need it in the next step.
Create an IAM policy
The next step is to create an IAM policy which allows 'read' access to the newly created secret.
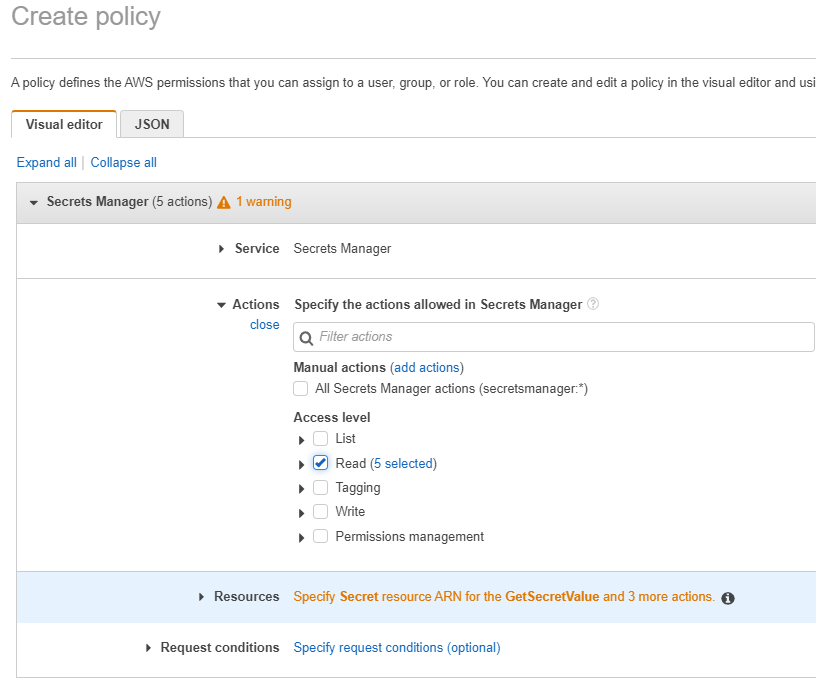
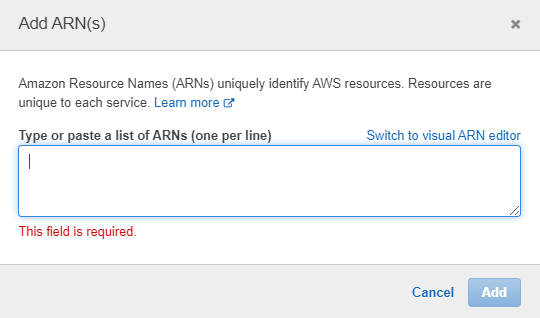
Note, only read access has been selected. Expand the 'Specify Secret Resource..' and click the link to add ARNs of the secrets.
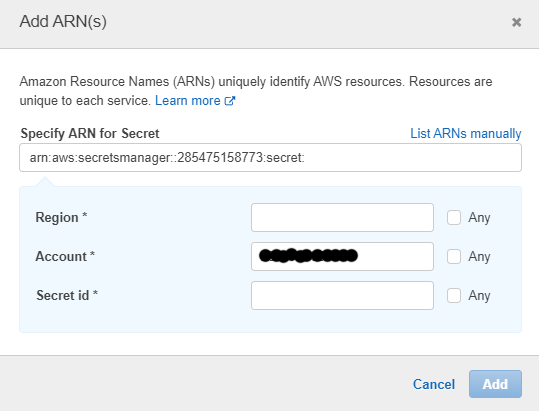
Click the 'List ARNs Manually' link to directly enter the ARN we copied earlier.
Create the IAM role
The next step is to create an IAM role to allow EC2 instances access the secret stored in the Secrets Manager via the role created in the previous step.
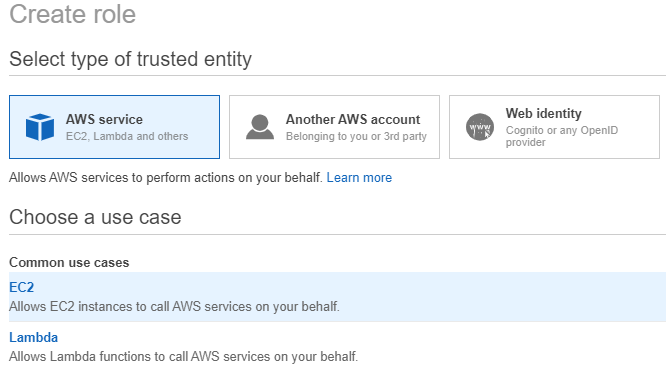
Note, we have selected EC2 in the above screenshot.
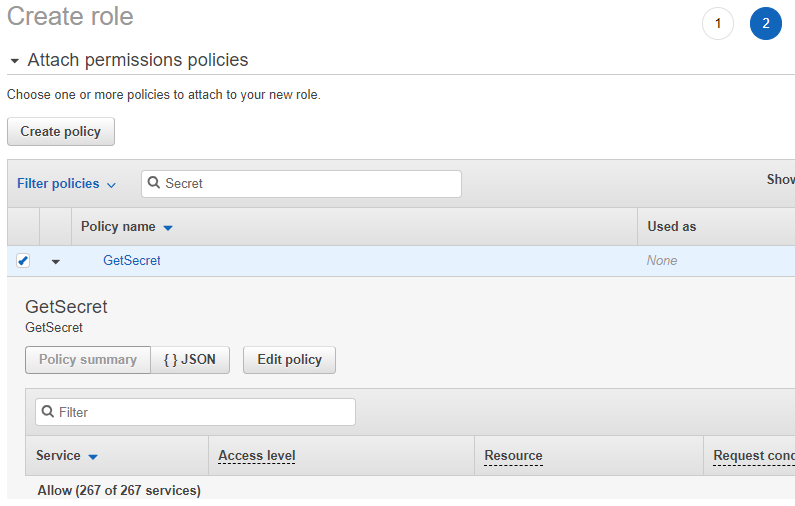
Select the policy we created in earlier, the policy is named 'GetSecret' in this example. Click 'Next: Tags' to proceed to the next screen. Click 'Next: Review' to move to the final screen.
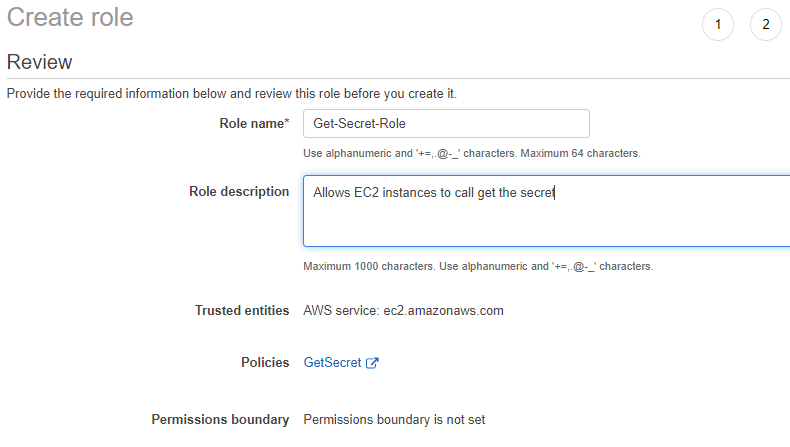
Finally we provide the role name and a description and create the role. Click 'Create role' button.
Accessing the secret from Java
If you noticed, when you create a secret in AWS Secrets Manager, the console shows you sample code in various languages like Java, C#, Go etc. that you can use to read the secret. The code here is based on this same code.
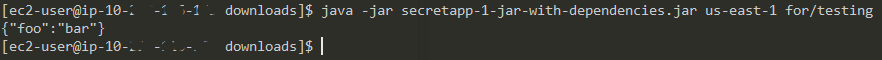
The application is a simple console application which expects two arguements, the AWS region and the secret name. The source code is available on GiHub.
Running the code on an EC2 instance
The next step is the run the application on an EC2 instance. Spin up an EC2 instance, build the application and copy the jar file to the EC2 instance. If you now run the application, you'll see an error like this:
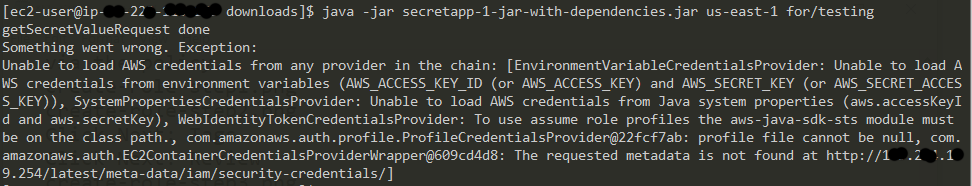
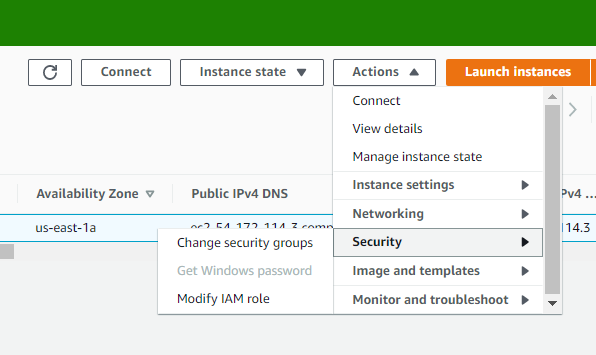
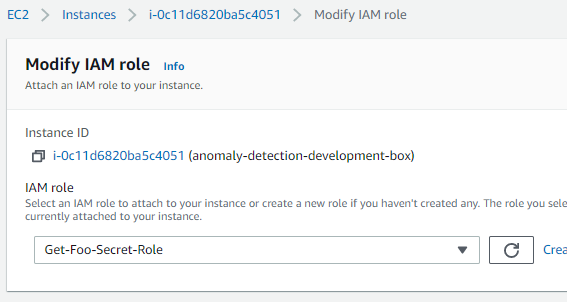
Why is this happening? We forgot the last thing which is to attach the IAM role we created to the EC2 instance. Navigate to EC2 dashboard in the AWS Management Console, select the EC2 instance and attach the IAM role we created.
We we now rerun the application we see: